Publications
2024
-
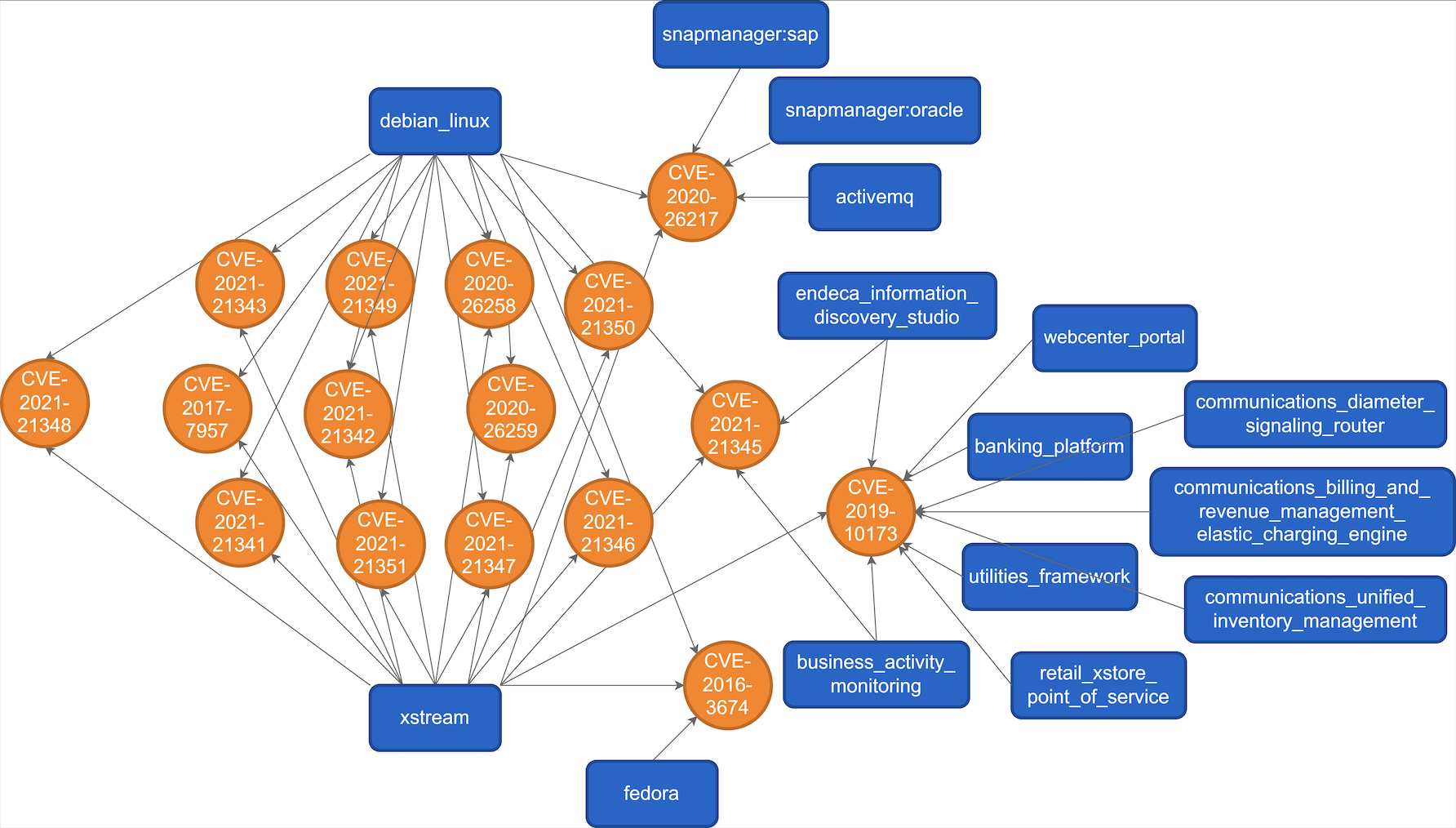 Uncovering CWE-CVE-CPE Relations with Threat Knowledge GraphsZhenpeng Shi, Nikolay Matyunin, Kalman Graffi, and David StarobinskiACM Transactions on Privacy and Security, Feb 2024
Uncovering CWE-CVE-CPE Relations with Threat Knowledge GraphsZhenpeng Shi, Nikolay Matyunin, Kalman Graffi, and David StarobinskiACM Transactions on Privacy and Security, Feb 2024Security assessment relies on public information about products, vulnerabilities, and weaknesses. So far, databases in these categories have rarely been analyzed in combination. Yet, doing so could help predict unreported vulnerabilities and identify common threat patterns. In this article, we propose a methodology for producing and optimizing a knowledge graph that aggregates knowledge from common threat databases (CVE, CWE, and CPE). We apply the threat knowledge graph to predict associations between threat databases, specifically between products, vulnerabilities, and weaknesses. We evaluate the prediction performance both in closed world with associations from the knowledge graph and in open world with associations revealed afterward. Using rank-based metrics (i.e., Mean Rank, Mean Reciprocal Rank, and Hits@N scores), we demonstrate the ability of the threat knowledge graph to uncover many associations that are currently unknown but will be revealed in the future, which remains useful over different time periods. We propose approaches to optimize the knowledge graph and show that they indeed help in further uncovering associations. We have made the artifacts of our work publicly available.
@article{Shi2024, title = {Uncovering {{CWE-CVE-CPE Relations}} with {{Threat Knowledge Graphs}}}, author = {Shi, Zhenpeng and Matyunin, Nikolay and Graffi, Kalman and Starobinski, David}, year = {2024}, month = feb, journal = {ACM Transactions on Privacy and Security}, volume = {27}, number = {1}, pages = {13:1--13:26}, issn = {2471-2566}, doi = {10.1145/3641819}, }
2022
-
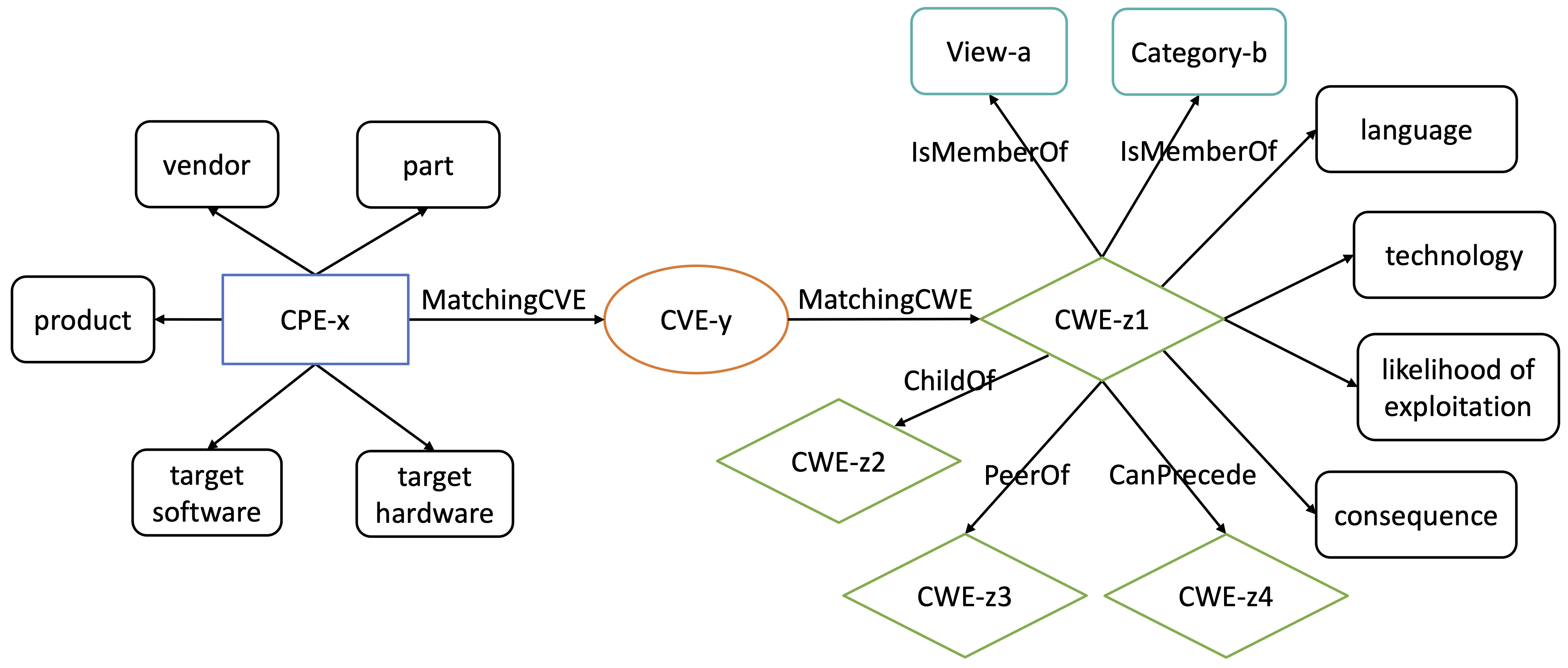 Uncovering Product Vulnerabilities with Threat Knowledge GraphsZhenpeng Shi, Nikolay Matyunin, Kalman Graffi, and David StarobinskiIn 2022 IEEE Secure Development Conference (SecDev), Dec 2022
Uncovering Product Vulnerabilities with Threat Knowledge GraphsZhenpeng Shi, Nikolay Matyunin, Kalman Graffi, and David StarobinskiIn 2022 IEEE Secure Development Conference (SecDev), Dec 2022Threat modeling and security assessment rely on public information on products, vulnerabilities and weaknesses. So far, databases in these categories have rarely been analyzed in combination. Yet, doing so could help predict unreported vulnerabilities and identify common threat patterns. In this paper, we propose a methodology for producing and optimizing a knowledge graph that aggregates knowledge from common threat databases (CPE, CVE, and CWE). We apply the threat knowledge graph to predict associations between threat databases, specifically between products and vulnerabilities. We evaluate the prediction performance based on historical data, using precision, recall, and F1-score metrics. We demonstrate the ability of the threat knowledge graph to uncover many associations that are currently unknown but will be revealed in the future.
@inproceedings{Shi2022a, title = {Uncovering {{Product Vulnerabilities}} with {{Threat Knowledge Graphs}}}, booktitle = {2022 {{IEEE Secure Development Conference}} ({{SecDev}})}, author = {Shi, Zhenpeng and Matyunin, Nikolay and Graffi, Kalman and Starobinski, David}, year = {2022}, month = dec, pages = {84--90}, doi = {10.1109/SecDev53368.2022.00028}, } -
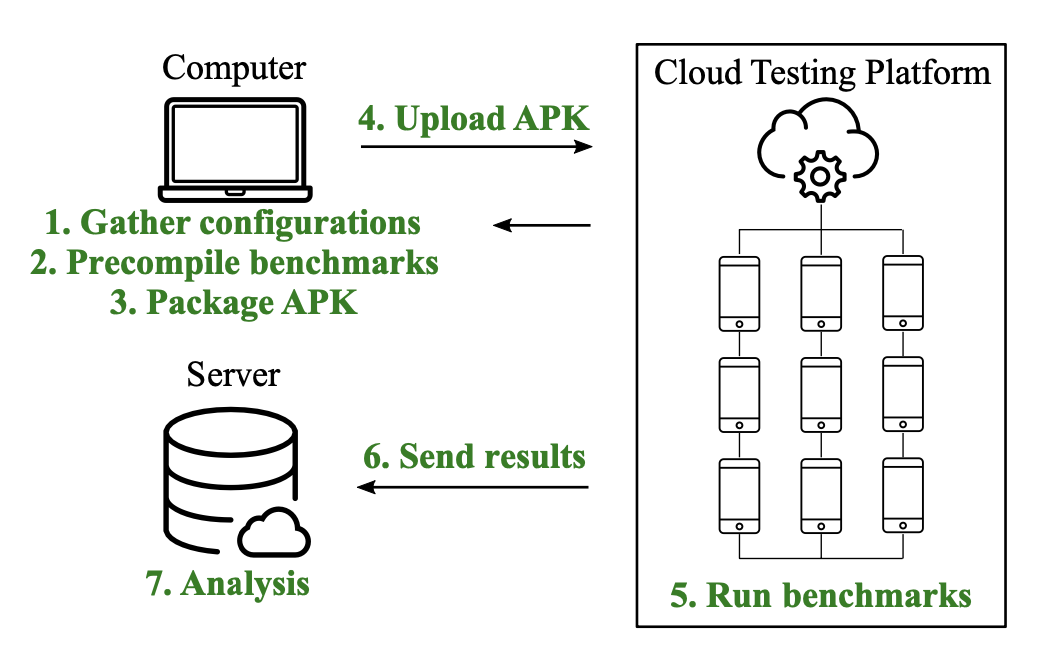 Evaluation of Cache Attacks on Arm Processors and Secure CachesShuwen Deng, Nikolay Matyunin, Wenjie Xiong, Stefan Katzenbeisser, and Jakub SzeferIEEE Transactions on Computers, Sep 2022
Evaluation of Cache Attacks on Arm Processors and Secure CachesShuwen Deng, Nikolay Matyunin, Wenjie Xiong, Stefan Katzenbeisser, and Jakub SzeferIEEE Transactions on Computers, Sep 2022Timing-based side and covert channels in processor caches continue to be a threat to modern computers. This work shows for the first time, a systematic, large-scale analysis of Arm devices and the detailed results of attacks the processors are vulnerable to. Compared to x86, Arm uses different architectures, microarchitectural implementations, cache replacement policies, etc., which affects how attacks can be launched, and how security testing for the vulnerabilities should be done. To evaluate security, this paper presents security benchmarks specifically developed for testing Arm processors and their caches. The benchmarks are evaluated with sensitivity tests, which examine how sensitive the benchmarks are to having a correct configuration in the testing phase. Further, to evaluate a large number of devices, this work leverages a novel approach of using a cloud-based Arm device testbed for architectural and security research on timing channels and runs the benchmarks on 34 different physical devices. In parallel, there has been much interest in secure caches to defend the various attacks. Consequently, this paper also investigates secure cache architectures using proposed benchmarks. Especially, this paper implements and evaluates secure PL and RF caches, showing the security of PL and RF caches, but also uncovers new weaknesses.
@article{Deng2022, title = {Evaluation of {{Cache Attacks}} on {{Arm Processors}} and {{Secure Caches}}}, author = {Deng, Shuwen and Matyunin, Nikolay and Xiong, Wenjie and Katzenbeisser, Stefan and Szefer, Jakub}, year = {2022}, month = sep, journal = {IEEE Transactions on Computers}, volume = {71}, number = {9}, pages = {2248--2262}, issn = {1557-9956}, doi = {10.1109/TC.2021.3126150}, } -
 Threat Modeling Tools: A TaxonomyZhenpeng Shi, Kalman Graffi, David Starobinski, and Nikolay MatyuninIEEE Security & Privacy, Jul 2022
Threat Modeling Tools: A TaxonomyZhenpeng Shi, Kalman Graffi, David Starobinski, and Nikolay MatyuninIEEE Security & Privacy, Jul 2022Threat modeling tools allow for identifying weaknesses in a system’s design. Yet, understanding conceptual differences between the tools is not trivial. We propose a taxonomy of threat modeling tools, using it to compare several popular ones.
@article{Shi2022, title = {Threat {{Modeling Tools}}: {{A Taxonomy}}}, shorttitle = {Threat {{Modeling Tools}}}, author = {Shi, Zhenpeng and Graffi, Kalman and Starobinski, David and Matyunin, Nikolay}, year = {2022}, month = jul, journal = {IEEE Security \& Privacy}, volume = {20}, number = {4}, pages = {29--39}, issn = {1558-4046}, doi = {10.1109/MSEC.2021.3125229}, } -
 Sensor-Based Covert Channels on Mobile DevicesNikolay MatyuninTechnical University of Darmstadt, Germany, Jul 2022
Sensor-Based Covert Channels on Mobile DevicesNikolay MatyuninTechnical University of Darmstadt, Germany, Jul 2022Smartphones have become ubiquitous in our daily activities, having billions of active users worldwide. The wide range of functionalities of modern mobile devices is enriched by many embedded sensors. These sensors, accessible by third-party mobile applications, pose novel security and privacy threats to the users of the devices. Numerous research works demonstrate that user keystrokes, location, or even speech can be inferred based on sensor measurements. Furthermore, the sensor itself can be susceptible to external physical interference, which can lead to attacks on systems that rely on sensor data. In this dissertation, we investigate how reaction of sensors in mobile devices to malicious physical interference can be exploited to establish covert communication channels between otherwise isolated devices or processes. We present multiple covert channels that use sensors? reaction to electromagnetic and acoustic interference to transmit sensitive data from nearby devices with no dedicated equipment or hardware modifications. In addition, these covert channels can also transmit information between applications within a mobile device, breaking the logical isolation enforced by the operating system. Furthermore, we discuss how sensor-based covert channels can affect privacy of end users by tracking their activities on two different devices or across two different applications on the same device. Finally, we present a framework that automatically identifies covert channels that are based on physical interference between hardware components of mobile devices. As a result of the experimental evaluation, we can confirm previously known covert channels on smartphones, and discover novel sources of cross-component interference that can be used to establish covert channels. Focusing on mobile platforms in this work, we aim to show that it is of crucial importance to consider physical covert channels when assessing the security of the systems that rely on sensors, and advocate for holistic approaches that can proactively identify and estimate corresponding security and privacy risks.
@phdthesis{Matyunin2022, title = {Sensor-{{Based Covert Channels}} on {{Mobile Devices}}}, author = {Matyunin, Nikolay}, year = {2022}, month = jul, address = {Darmstadt}, school = {Technical University of Darmstadt, Germany}, doi = {https://doi.org/10.26083/tuprints-00021975}, url = {http://tuprints.ulb.tu-darmstadt.de/21975/}, } -
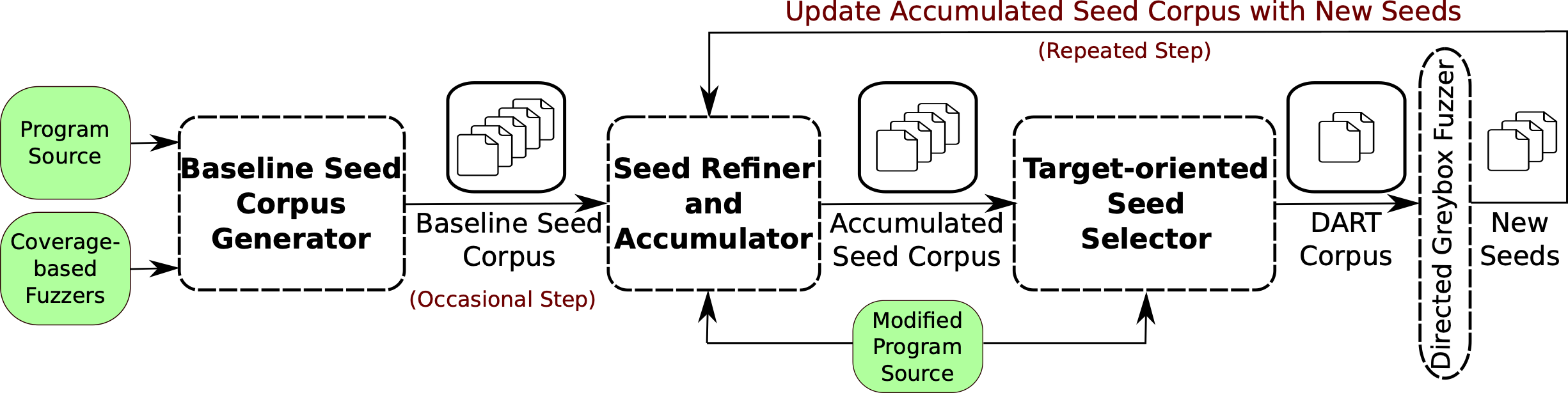 TargetFuzz: Using DARTs to Guide Directed Greybox FuzzersSadullah Canakci, Nikolay Matyunin, Kalman Graffi, Ajay Joshi, and Manuel EgeleIn Proceedings of the 2022 ACM on Asia Conference on Computer and Communications Security, May 2022
TargetFuzz: Using DARTs to Guide Directed Greybox FuzzersSadullah Canakci, Nikolay Matyunin, Kalman Graffi, Ajay Joshi, and Manuel EgeleIn Proceedings of the 2022 ACM on Asia Conference on Computer and Communications Security, May 2022Software development is a continuous and incremental process. Developers continuously improve their software in small batches rather than in one large batch. The high frequency of small batches makes it essential to use effective testing methods that detect bugs under limited testing time. To this end, researchers propose directed greybox fuzzing (DGF) which aims to generate test cases towards stressing certain target sites. Different from the coverage-based greybox fuzzing (CGF) which aims to maximize code coverage in the whole program, the goal of DGF is to cover potentially buggy code regions (e.g., a recently modified program region). While prior works improve several aspects of DGF (such as power scheduling, input prioritization, and target selection), little attention has been given to improving the seed selection process. Existing DGF tools use seed corpora mainly tailored for CGF (i.e., a set of seeds that cover different regions of the program). We observe that using CGF-based corpora limits the bug-finding capability of a directed greybox fuzzer. To mitigate this shortcoming, we propose TargetFuzz, a mechanism that provides a DGF tool with a target-oriented seed corpus. We refer to this corpus as DART corpus, which contains only ’close’ seeds to the targets. This way, DART corpus guides DGF to the targets, thereby exposing bugs even under limited fuzzing time. Evaluations on 34 real bugs show that AFLGo (a state-of-the-art directed greybox fuzzer), when equipped with DART corpus, finds 10 additional bugs and achieves $4.03x speedup, on average, in the time-to-exposure compared to a generic CGF-based corpus.
@inproceedings{Canakci2022, title = {{{TargetFuzz}}: {{Using DARTs}} to {{Guide Directed Greybox Fuzzers}}}, shorttitle = {{{TargetFuzz}}}, booktitle = {Proceedings of the 2022 {{ACM}} on {{Asia Conference}} on {{Computer}} and {{Communications Security}}}, author = {Canakci, Sadullah and Matyunin, Nikolay and Graffi, Kalman and Joshi, Ajay and Egele, Manuel}, year = {2022}, month = may, series = {{{ASIA CCS}} '22}, pages = {561--573}, publisher = {Association for Computing Machinery}, address = {New York, NY, USA}, doi = {10.1145/3488932.3501276}, isbn = {978-1-4503-9140-5}, }
2019
-
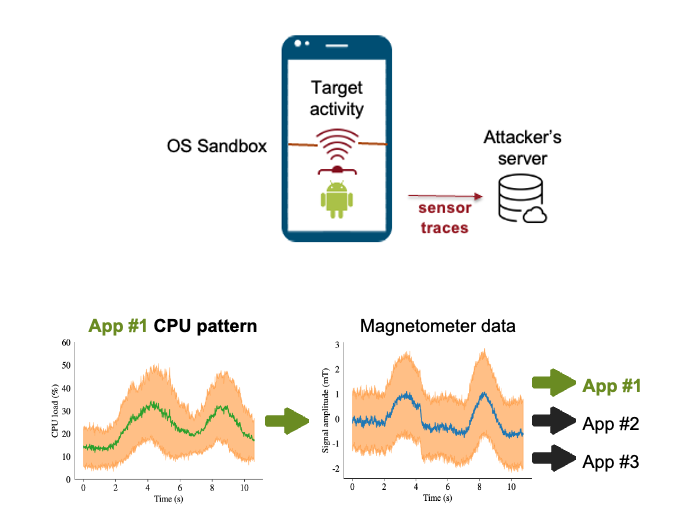 MagneticSpy: Exploiting Magnetometer in Mobile Devices for Website and Application FingerprintingNikolay Matyunin, Yujue Wang, Tolga Arul, Kristian Kullmann, Jakub Szefer, and Stefan KatzenbeisserIn Proceedings of the 18th ACM Workshop on Privacy in the Electronic Society, Nov 2019
MagneticSpy: Exploiting Magnetometer in Mobile Devices for Website and Application FingerprintingNikolay Matyunin, Yujue Wang, Tolga Arul, Kristian Kullmann, Jakub Szefer, and Stefan KatzenbeisserIn Proceedings of the 18th ACM Workshop on Privacy in the Electronic Society, Nov 2019Recent studies have shown that aggregate CPU usage and power consumption traces on smartphones can leak information about applications running on the system or websites visited. In response, access to such data has been blocked for mobile applications starting from Android 8. In this work, we explore a new source of side-channel leakage for this class of attacks. Our method is based on the fact that electromagnetic activity caused by mobile processors leads to noticeable disturbances in magnetic sensor measurements on mobile devices, with the amplitude being proportional to the CPU workload. Therefore, recorded sensor data can be analyzed to reveal information about ongoing activities. The attack works on a number of devices: we evaluated 80 models of modern smartphones and tablets and observed the reaction of the magnetometer to the CPU activity on 56 of them. On selected devices we were able to successfully identify which application has been opened (with up to 90% accuracy) or which web page has been loaded (up to 91% accuracy). The presented side channel poses a significant risk to end users’ privacy, as the sensor data can be recorded from native apps or even from web pages without user permissions. Finally, we discuss possible countermeasures to prevent the presented information leakage.
@inproceedings{Matyunin2019a, title = {{{MagneticSpy}}: {{Exploiting Magnetometer}} in {{Mobile Devices}} for {{Website}} and {{Application Fingerprinting}}}, shorttitle = {{{MagneticSpy}}}, booktitle = {Proceedings of the 18th {{ACM Workshop}} on {{Privacy}} in the {{Electronic Society}}}, author = {Matyunin, Nikolay and Wang, Yujue and Arul, Tolga and Kullmann, Kristian and Szefer, Jakub and Katzenbeisser, Stefan}, year = {2019}, month = nov, series = {{{WPES}}'19}, pages = {135--149}, publisher = {Association for Computing Machinery}, address = {New York, NY, USA}, doi = {10.1145/3338498.3358650}, isbn = {978-1-4503-6830-8}, } -
 Vibrational Covert Channels Using Low-Frequency Acoustic SignalsNikolay Matyunin, Yujue Wang, and Stefan KatzenbeisserIn Proceedings of the ACM Workshop on Information Hiding and Multimedia Security, Jul 2019
Vibrational Covert Channels Using Low-Frequency Acoustic SignalsNikolay Matyunin, Yujue Wang, and Stefan KatzenbeisserIn Proceedings of the ACM Workshop on Information Hiding and Multimedia Security, Jul 2019In this paper, we examine how acoustic signals in sub-bass and infrasonic range can be used to establish a vibrational covert channel between speaker-equipped computers and mobile devices. We show that typical consumer speakers are capable of producing low-frequency sounds, which are not perceivable by humans. At the same time, we show that producing such sounds by the speaker’s woofer inevitably generates slight vibrations of the speaker and the surface where it is located. Being unnoticeable to people, such vibrations can be captured by the accelerometer sensor of a mobile device located on the same surface. Therefore, information can be encoded into low-frequency sounds played by a speaker and received on a mobile device by analyzing the produced vibrations. Note that access to the accelerometer on modern mobile devices does not require any user permissions, making the transmission completely unnoticeable. We evaluate the presented covert channel for different speakers, apply it to several application scenarios, and give an overview of possible countermeasures.
@inproceedings{Matyunin2019, title = {Vibrational {{Covert Channels}} Using {{Low-Frequency Acoustic Signals}}}, booktitle = {Proceedings of the {{ACM Workshop}} on {{Information Hiding}} and {{Multimedia Security}}}, author = {Matyunin, Nikolay and Wang, Yujue and Katzenbeisser, Stefan}, year = {2019}, month = jul, series = {{{IH}}\&{{MMSec}}'19}, pages = {31--36}, publisher = {Association for Computing Machinery}, address = {New York, NY, USA}, doi = {10.1145/3335203.3335712}, isbn = {978-1-4503-6821-6}, }
2018
-
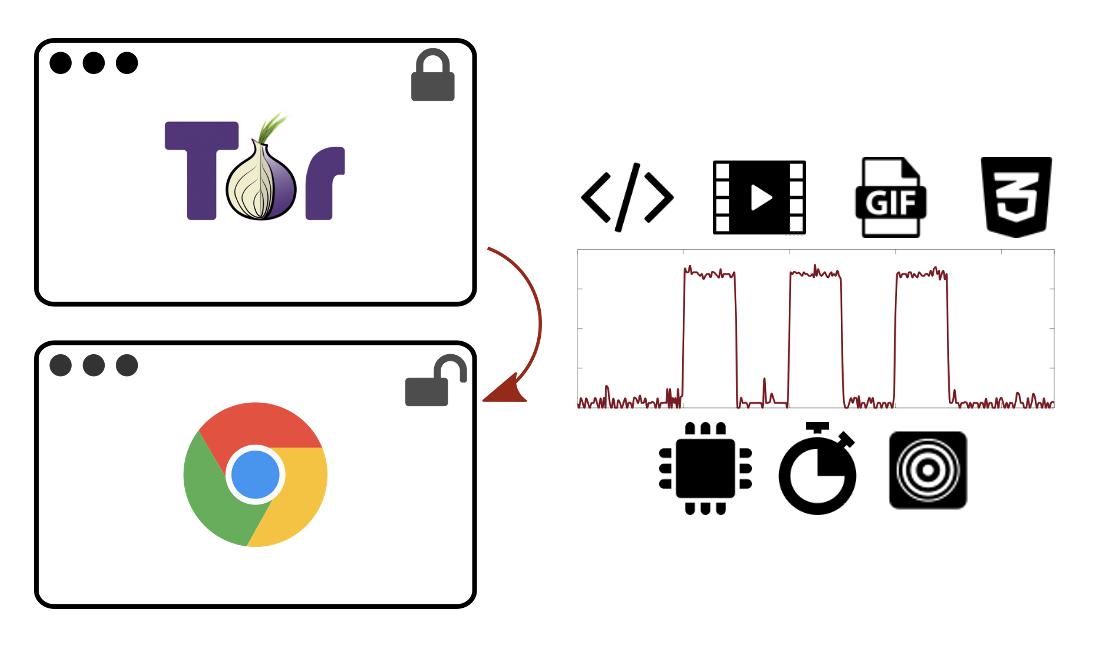 Tracking Private Browsing Sessions Using CPU-based Covert ChannelsNikolay Matyunin, Nikolaos A. Anagnostopoulos, Spyros Boukoros, Markus Heinrich, André Schaller, Maksim Kolinichenko, and Stefan KatzenbeisserIn Proceedings of the 11th ACM Conference on Security & Privacy in Wireless and Mobile Networks, Jun 2018
Tracking Private Browsing Sessions Using CPU-based Covert ChannelsNikolay Matyunin, Nikolaos A. Anagnostopoulos, Spyros Boukoros, Markus Heinrich, André Schaller, Maksim Kolinichenko, and Stefan KatzenbeisserIn Proceedings of the 11th ACM Conference on Security & Privacy in Wireless and Mobile Networks, Jun 2018In this paper we examine the use of covert channels based on CPU load in order to achieve persistent user identification through browser sessions. In particular, we demonstrate that an HTML5 video, a GIF image, or CSS animations on a webpage can be used to force the CPU to produce a sequence of distinct load levels, even without JavaScript or any client-side code.These load levels can be then captured either by another browsing session, running on the same or a different browser in parallel to the browsing session we want to identify, or by a malicious app installed on the device. To get a good estimation of the CPU load caused by the target session, the receiver can observe system statistics about CPU activity (app), or constantly measure time it takes to execute a known code segment (app and browser). Furthermore, for mobile devices we propose a sensor-based approach to estimate the CPU load, based on exploiting disturbances of the magnetometer sensor data caused by the high CPU activity.Captured loads can be decoded and translated into an identifying bit string, which is transmitted back to the attacker. Due to the way loads are produced, these methods are applicable even in highly restrictive browsers, such as the Tor Browser, and run unnoticeably to the end user. Therefore, unlike existing ways of web tracking, our methods circumvent most of the existing countermeasures, as they store the identifying information outside the browsing session being targeted.Finally, we also thoroughly evaluate and assess each presented method of generating and receiving the signal, and provide an overview of potential countermeasures.
@inproceedings{Matyunin2018a, title = {Tracking {{Private Browsing Sessions}} Using {{CPU-based Covert Channels}}}, booktitle = {Proceedings of the 11th {{ACM Conference}} on {{Security}} \& {{Privacy}} in {{Wireless}} and {{Mobile Networks}}}, author = {Matyunin, Nikolay and Anagnostopoulos, Nikolaos A. and Boukoros, Spyros and Heinrich, Markus and Schaller, Andr{\'e} and Kolinichenko, Maksim and Katzenbeisser, Stefan}, year = {2018}, month = jun, series = {{{WiSec}} '18}, pages = {63--74}, publisher = {Association for Computing Machinery}, address = {New York, NY, USA}, doi = {10.1145/3212480.3212489}, isbn = {978-1-4503-5731-9}, } -
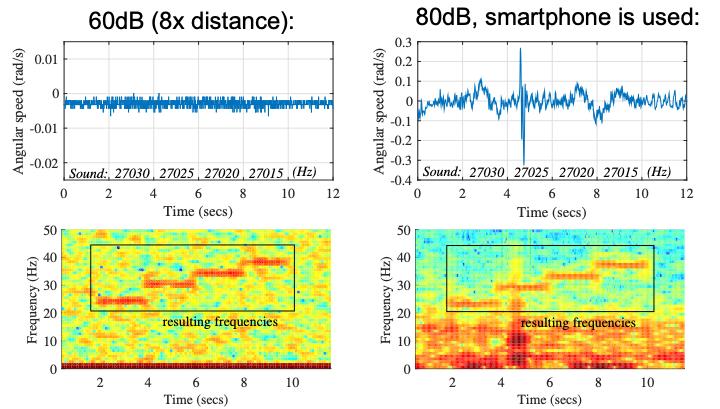 Zero-Permission Acoustic Cross-Device TrackingNikolay Matyunin, Jakub Szefer, and Stefan KatzenbeisserIn 2018 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Apr 2018
Zero-Permission Acoustic Cross-Device TrackingNikolay Matyunin, Jakub Szefer, and Stefan KatzenbeisserIn 2018 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Apr 2018Adversaries today can embed tracking identifiers into ultrasonic sound and covertly transmit them between devices without users realizing that this is happening. To prevent such emerging privacy risks, mobile applications now require a request for an explicit user permission, at run-time, to get access to a device’s microphone. In this paper, however, we show that current defenses are not enough. We introduce a novel approach to acoustic cross-device tracking, which does not require microphone access, but instead exploits the susceptibility of MEMS gyroscopes to acoustic vibrations at specific (ultrasonic) frequencies. Currently, no permissions are needed to access the gyroscope’s data, and the gyroscope can be accessed from apps or even from a web browser. In this manner, gyroscopes in modern smartphones and smartwatches can be used as zero-permission receivers of ultrasonic signals, making cross-device tracking completely unnoticeable to users. We evaluate our approach on several mobile devices using different audio hardware, achieving 10-20bit/s transmission bandwidth at distances from 35cm to 16m in realistic attack scenarios. Finally, we discuss potential countermeasures against the presented attack.
@inproceedings{Matyunin2018, title = {Zero-Permission Acoustic Cross-Device Tracking}, booktitle = {2018 {{IEEE International Symposium}} on {{Hardware Oriented Security}} and {{Trust}} ({{HOST}})}, author = {Matyunin, Nikolay and Szefer, Jakub and Katzenbeisser, Stefan}, year = {2018}, month = apr, pages = {25--32}, doi = {10.1109/HST.2018.8383887}, }
2016
-
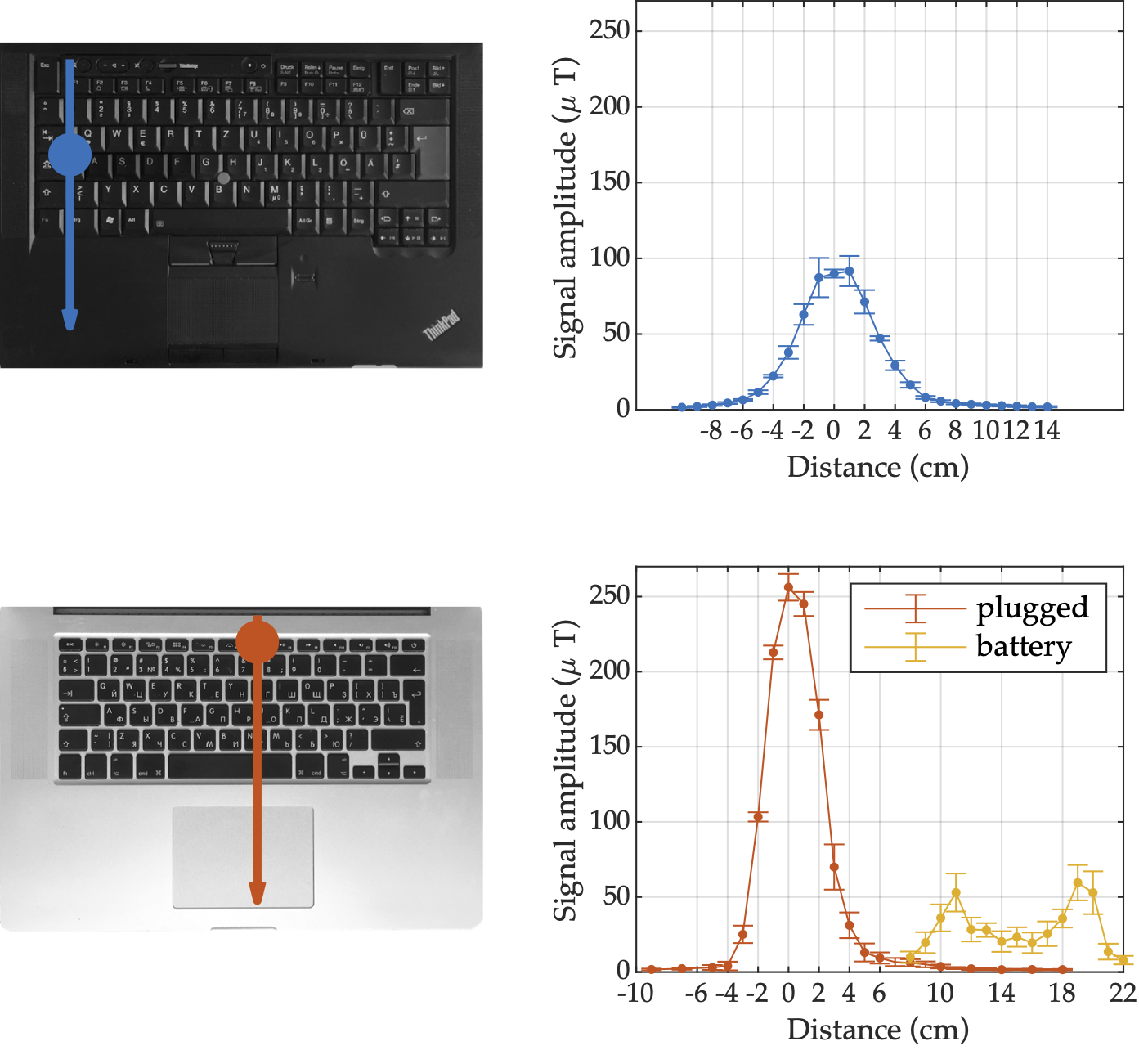 Covert Channels Using Mobile Device’s Magnetic Field SensorsNikolay Matyunin, Jakub Szefer, Sebastian Biedermann, and Stefan KatzenbeisserIn 2016 21st Asia and South Pacific Design Automation Conference (ASP-DAC), Jan 2016
Covert Channels Using Mobile Device’s Magnetic Field SensorsNikolay Matyunin, Jakub Szefer, Sebastian Biedermann, and Stefan KatzenbeisserIn 2016 21st Asia and South Pacific Design Automation Conference (ASP-DAC), Jan 2016This paper presents a new covert channel using smartphone magnetic sensors. We show that modern smartphones are capable to detect the magnetic field changes induced by different computer components during I/O operations. In particular, we are able to create a covert channel between a laptop and a mobile device without any additional equipment, firmware modifications or privileged access on either of the devices. We present two encoding schemes for the covert channel communication and evaluate their effectiveness.
@inproceedings{Matyunin2016, title = {Covert Channels Using Mobile Device's Magnetic Field Sensors}, booktitle = {2016 21st {{Asia}} and {{South Pacific Design Automation Conference}} ({{ASP-DAC}})}, author = {Matyunin, Nikolay and Szefer, Jakub and Biedermann, Sebastian and Katzenbeisser, Stefan}, year = {2016}, month = jan, pages = {525--532}, issn = {2153-697X}, doi = {10.1109/ASPDAC.2016.7428065}, }